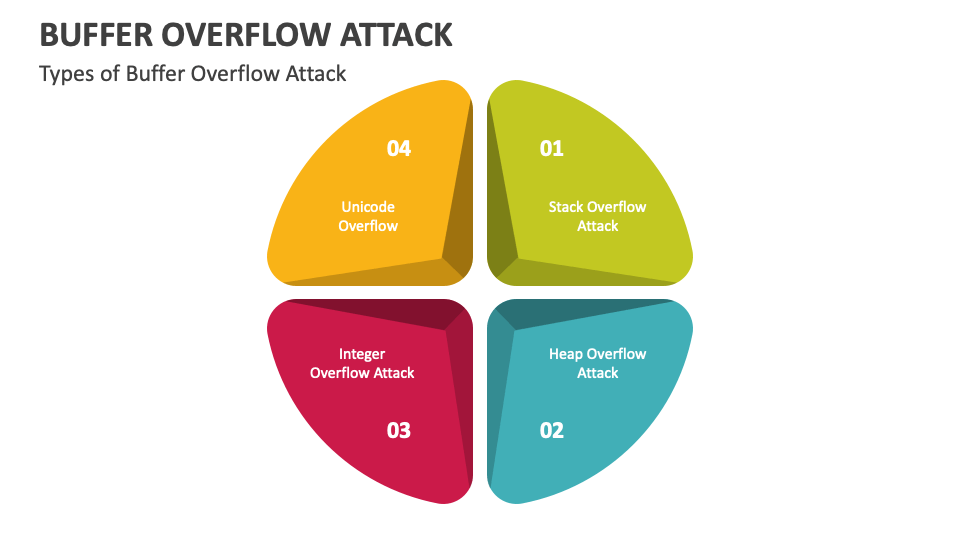
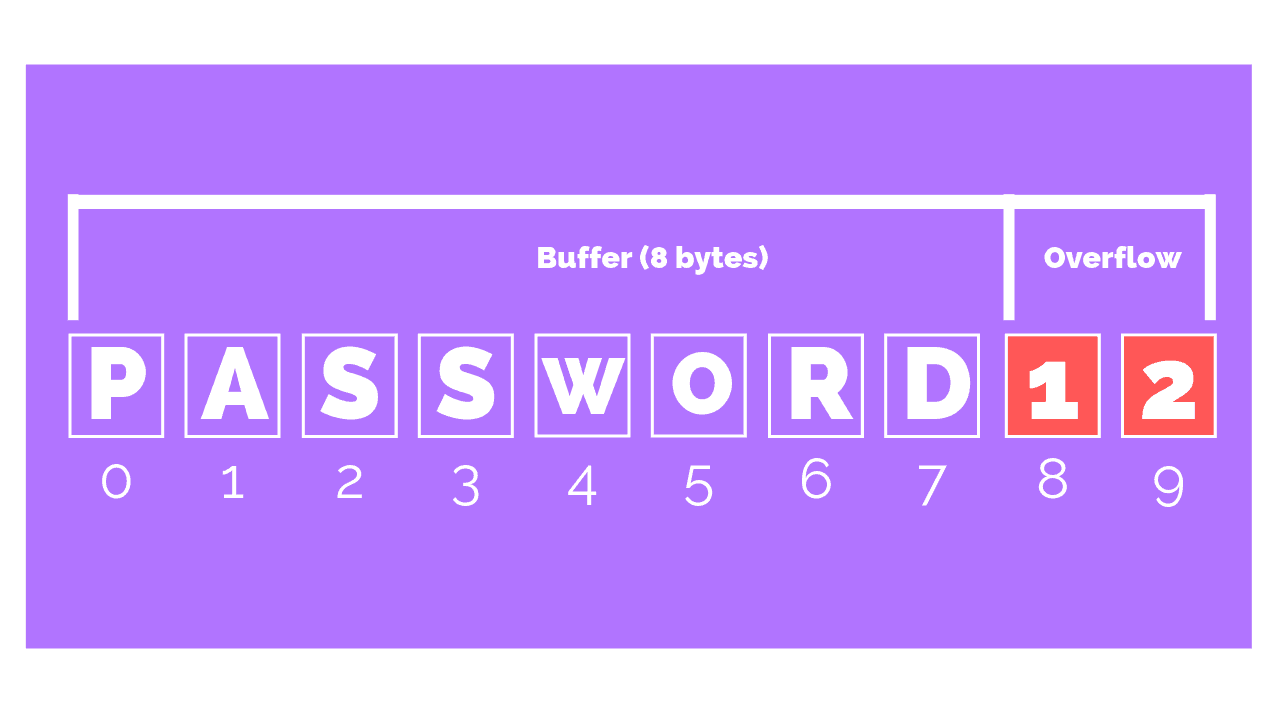
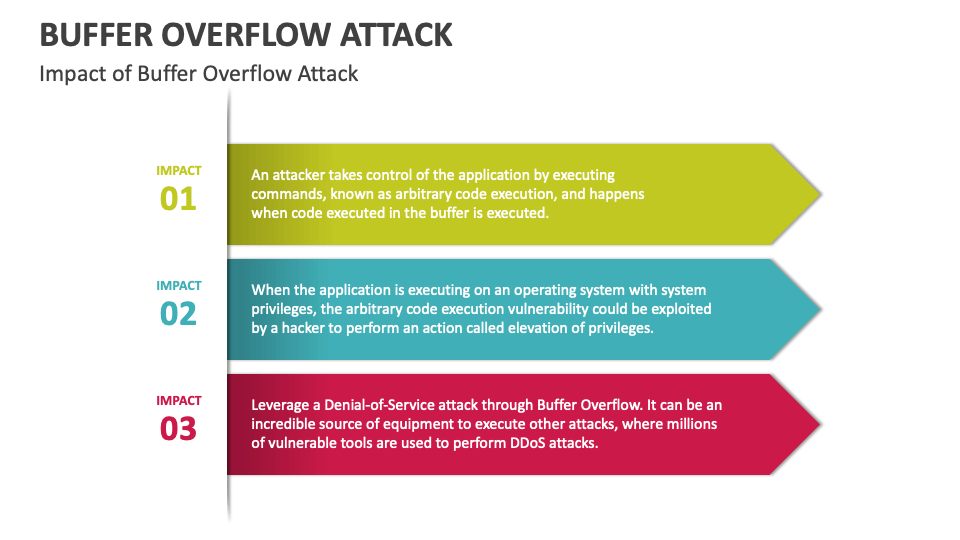
Is A Form Of Overflow Attack - The code above shows an example of a buffer overflow on the. The __________ used a buffer overflow exploit in. _________ is a form of overflow attack. Buffer overflow is probably the best known form of software security vulnerability. Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate. Most software developers know what a buffer overflow.
Buffer overflow is probably the best known form of software security vulnerability. Most software developers know what a buffer overflow. The code above shows an example of a buffer overflow on the. Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate. The __________ used a buffer overflow exploit in. _________ is a form of overflow attack.
The __________ used a buffer overflow exploit in. The code above shows an example of a buffer overflow on the. Most software developers know what a buffer overflow. Buffer overflow is probably the best known form of software security vulnerability. _________ is a form of overflow attack. Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate.
Buffer Overflow Attack PowerPoint and Google Slides Template PPT Slides
Buffer overflow is probably the best known form of software security vulnerability. The __________ used a buffer overflow exploit in. _________ is a form of overflow attack. Most software developers know what a buffer overflow. Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate.
How To Prevent A Buffer Overflow Attack
Most software developers know what a buffer overflow. _________ is a form of overflow attack. Buffer overflow is probably the best known form of software security vulnerability. The code above shows an example of a buffer overflow on the. Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate.
Buffer Overflow Attack CyberHoot
The __________ used a buffer overflow exploit in. The code above shows an example of a buffer overflow on the. Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate. Most software developers know what a buffer overflow. _________ is a form of overflow attack.
Buffer Overflow Attack Glossary & Definition
The __________ used a buffer overflow exploit in. Buffer overflow is probably the best known form of software security vulnerability. _________ is a form of overflow attack. Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate. Most software developers know what a buffer overflow.
Buffer Overflow Attack PowerPoint and Google Slides Template PPT Slides
Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate. Buffer overflow is probably the best known form of software security vulnerability. The code above shows an example of a buffer overflow on the. _________ is a form of overflow attack. The __________ used a buffer overflow exploit in.
What is a buffer overflow attack? NordVPN
Buffer overflow is probably the best known form of software security vulnerability. The __________ used a buffer overflow exploit in. Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate. Most software developers know what a buffer overflow. The code above shows an example of a buffer overflow on.
What is a buffer overflow attack? Attack, Types & Vulnerabilities
Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate. The __________ used a buffer overflow exploit in. The code above shows an example of a buffer overflow on the. Buffer overflow is probably the best known form of software security vulnerability. Most software developers know what a buffer.
Buffer Overflow Attack
The __________ used a buffer overflow exploit in. Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate. _________ is a form of overflow attack. The code above shows an example of a buffer overflow on the. Buffer overflow is probably the best known form of software security vulnerability.
Buffer Overflow Attack PowerPoint and Google Slides Template PPT Slides
Buffer overflow is probably the best known form of software security vulnerability. Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate. _________ is a form of overflow attack. The __________ used a buffer overflow exploit in. Most software developers know what a buffer overflow.
GitHub inug4mi/overflowattack
Buffer overflow is probably the best known form of software security vulnerability. Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate. The code above shows an example of a buffer overflow on the. The __________ used a buffer overflow exploit in. _________ is a form of overflow attack.
Buffer Overflow Is Probably The Best Known Form Of Software Security Vulnerability.
The code above shows an example of a buffer overflow on the. _________ is a form of overflow attack. Most software developers know what a buffer overflow. Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate.