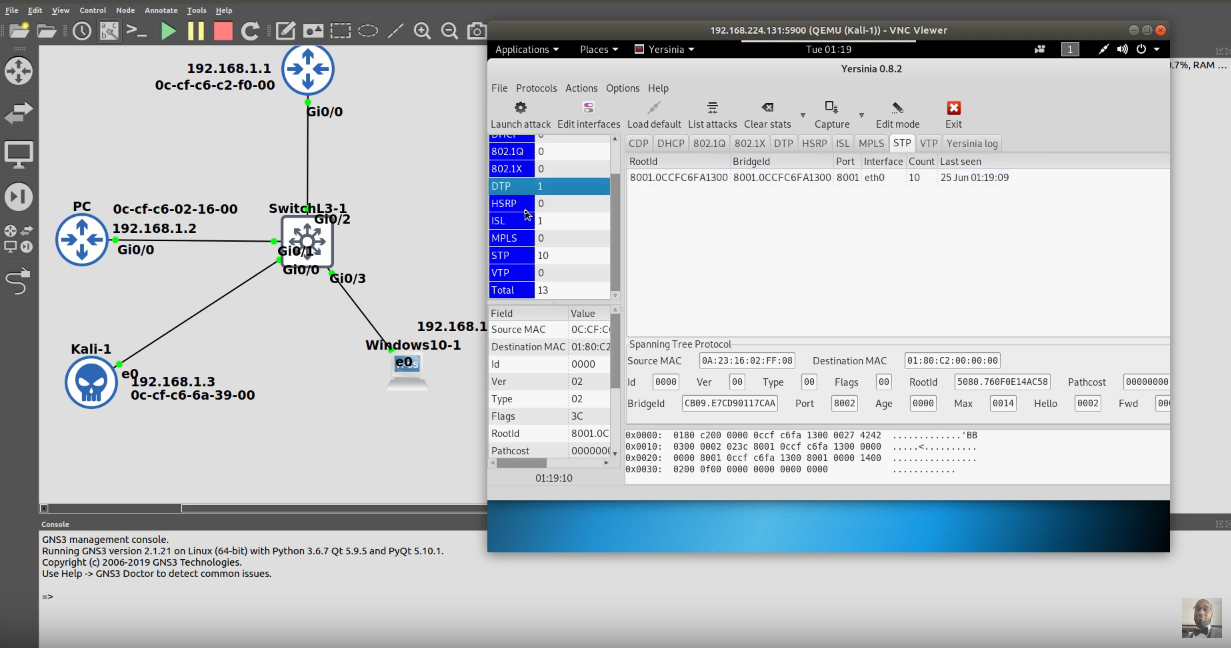
What Is A Method To Launch A Vlan Hopping Attack - What is a method to launch a vlan hopping attack? Introducing a rogue switch and enabling trunking; Sending spoofed native vlan information; What is a method to launch a vlan hopping attack? Introducing a rogue switch and enabling trunking; Use isl encapsulation on all trunk links. Sending spoofed native vlan information; This tag allows the frame to be forwarded to a vlan that the original 802.1q tag did not specify. A vlan hopping attack enables traffic from one vlan to be seen by another vlan without the aid of a router. In a basic vlan hopping attack, the.
What is a method to launch a vlan hopping attack? Use isl encapsulation on all trunk links. Introducing a rogue switch and enabling trunking; Sending spoofed native vlan information; Use vlan 1 as the native vlan on trunk ports. Introducing a rogue switch and enabling trunking; In a basic vlan hopping attack, the. What is a method to launch a vlan hopping attack? Sending spoofed ip addresses from. Disable stp on all nontrunk ports.
Sending spoofed native vlan information; A vlan hopping attack enables traffic from one vlan to be seen by another vlan without the aid of a router. What is a method to launch a vlan hopping attack? In a basic vlan hopping attack, the. What is the best way to prevent a vlan hopping attack? Introducing a rogue switch and enabling trunking; Use isl encapsulation on all trunk links. Use vlan 1 as the native vlan on trunk ports. Sending spoofed ip addresses from. Disable stp on all nontrunk ports.
VLAN Hopping Attack Network Security, Hopping, Traffic, Networking
Use vlan 1 as the native vlan on trunk ports. What is a method to launch a vlan hopping attack? In a basic vlan hopping attack, the. This tag allows the frame to be forwarded to a vlan that the original 802.1q tag did not specify. Use isl encapsulation on all trunk links.
VLAN Hopping How to defend your systems against attacks on a virtual LAN?
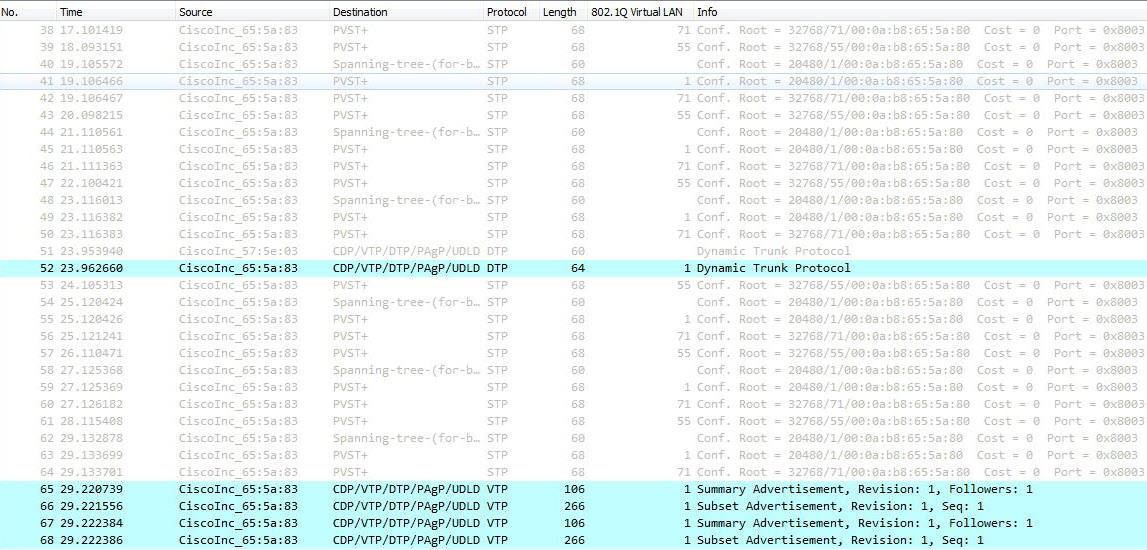
Sending spoofed native vlan information; Introducing a rogue switch and enabling trunking; What is a method to launch a vlan hopping attack? Introducing a rogue switch and enabling trunking; This tag allows the frame to be forwarded to a vlan that the original 802.1q tag did not specify.
VLAN hopping attack
Introducing a rogue switch and enabling trunking; Sending spoofed ip addresses from. This tag allows the frame to be forwarded to a vlan that the original 802.1q tag did not specify. In a basic vlan hopping attack, the. Introducing a rogue switch and enabling trunking;
What is VLAN Hopping Attack? Securium Solutions
Use isl encapsulation on all trunk links. Introducing a rogue switch and enabling trunking; What is a method to launch a vlan hopping attack? What is the best way to prevent a vlan hopping attack? Introducing a rogue switch and enabling trunking;
VLAN Hopping Attack PDF Architecture Computer Network
Disable stp on all nontrunk ports. A vlan hopping attack enables traffic from one vlan to be seen by another vlan without the aid of a router. In a basic vlan hopping attack, the. Sending spoofed native vlan information; What is a method to launch a vlan hopping attack?
Kali Linux VLAN Hopping Attack and How To Stop it Hacker
This tag allows the frame to be forwarded to a vlan that the original 802.1q tag did not specify. Sending spoofed ip addresses from. In a basic vlan hopping attack, the. What is a method to launch a vlan hopping attack? What is the best way to prevent a vlan hopping attack?
VLAN Hopping Defeats Segmentation Oversitesentry
What is a method to launch a vlan hopping attack? What is a method to launch a vlan hopping attack? Sending spoofed ip addresses from. Disable stp on all nontrunk ports. Use vlan 1 as the native vlan on trunk ports.
Vlan Hopping Attack PDF Computer Security Security
Use isl encapsulation on all trunk links. Sending spoofed ip addresses from. Sending spoofed native vlan information; Disable stp on all nontrunk ports. In a basic vlan hopping attack, the.
VLAN1 and Vlan Hopping Attack Blue Network Security
A vlan hopping attack enables traffic from one vlan to be seen by another vlan without the aid of a router. Disable stp on all nontrunk ports. This tag allows the frame to be forwarded to a vlan that the original 802.1q tag did not specify. Sending spoofed ip addresses from. Use isl encapsulation on all trunk links.
Sending Spoofed Native Vlan Information;
A vlan hopping attack enables traffic from one vlan to be seen by another vlan without the aid of a router. Sending spoofed native vlan information; What is a method to launch a vlan hopping attack? What is the best way to prevent a vlan hopping attack?
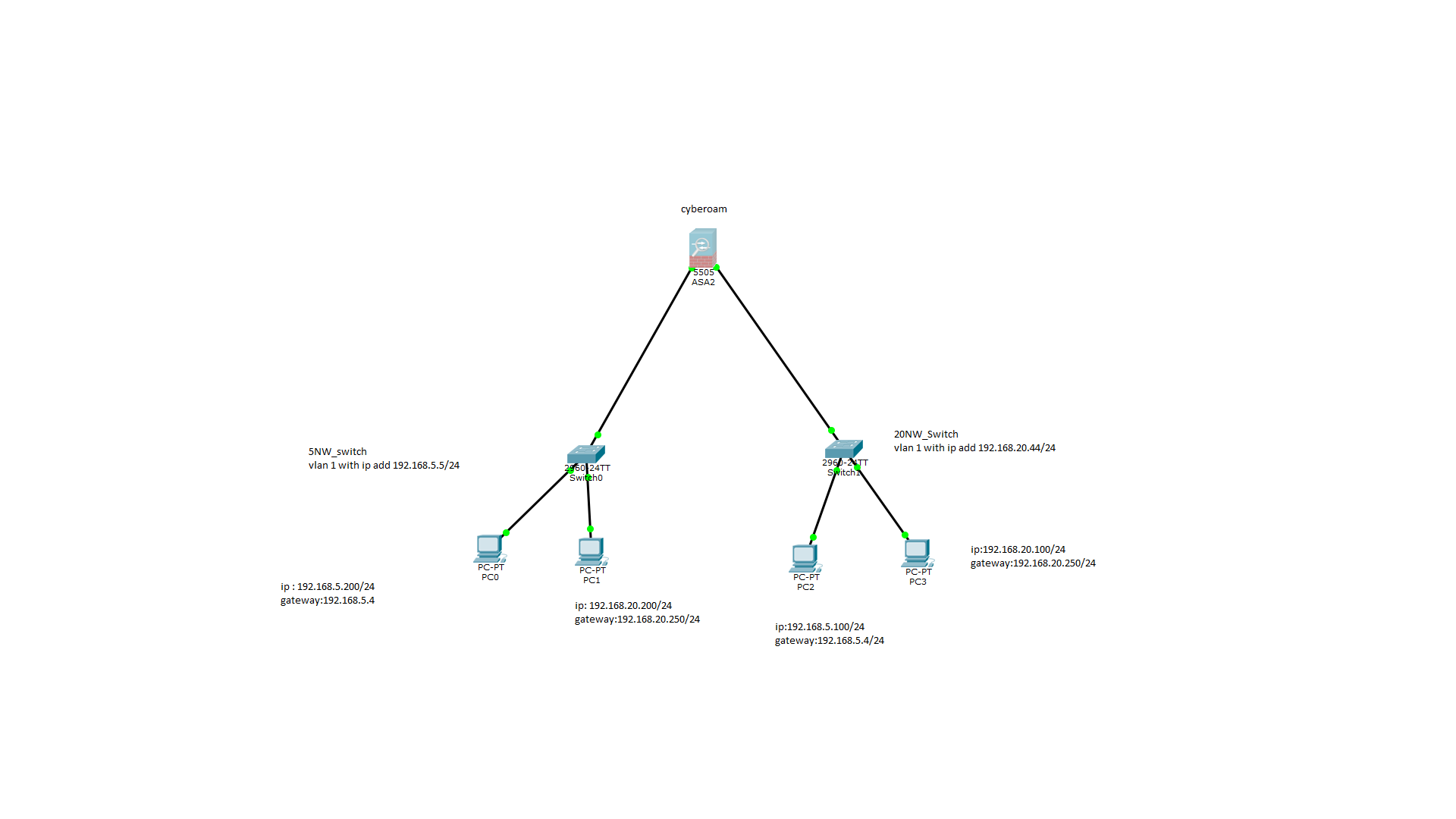
Use Vlan 1 As The Native Vlan On Trunk Ports.
What is a method to launch a vlan hopping attack? Use isl encapsulation on all trunk links. In a basic vlan hopping attack, the. Introducing a rogue switch and enabling trunking;
Introducing A Rogue Switch And Enabling Trunking;
Sending spoofed ip addresses from. This tag allows the frame to be forwarded to a vlan that the original 802.1q tag did not specify. Disable stp on all nontrunk ports.